IT execs also can get pleasure from seeing demonstrations of attacks to learn how data behaves especially cases. Take some time to check out demonstrations of the subsequent assaults:
Smurf assaults. A smurf attack usually takes benefit of the online market place Management Concept Protocol (ICMP), a interaction protocol accustomed to assess the status of the relationship between two devices.
Opposite to well known feeling, most DDoS attacks never entail superior levels of traffic. Under 1% of all DDoS assaults are volumetric. Volumetric attacks are simply just covered within the information additional often due to their sensational nature.
By clicking "Post" and publishing this type, I conform to get text messages, email messages and other communication regarding educational courses and alternatives, and also to be contacted by Yeshiva College and Everspring, its licensed consultant.
In accordance with new investigation DDOS assaults are not merely occurring additional often but are Long lasting for a longer period - up from minutes to days. This then has an important influence on business enterprise operations.
ICMP floods. Also known as “ping flood assaults,” these assaults bombard targets with ICMP echo requests from many spoofed IP addresses. The focused server have to reply to all of these requests and gets to be overloaded and unable to procedure valid ICMP echo requests.
Instruction and Schooling: Some portals may possibly offer you academic methods and coaching components to assist buyers improved have an understanding of DDoS assaults, ddos web their effect, and best procedures for safeguarding their on-line belongings.
Can it be Down At this time?: This source is a superb location to get started on when you suspect an assault. Check to check out no matter whether an internet site is down by getting into the domain which Device will return fast effects.
There exists an unknown connection situation between Cloudflare and the origin Website server. Therefore, the Online page can't be exhibited.
Contemporary software options will help figure out opportunity threats. A network stability and monitoring service can provide you with a warning to process modifications so that you can respond immediately.
CNAPP Secure almost everything from code to cloud more quickly with unparalleled context and visibility with just one unified platform.
Build specific protocols for backing up your info and using it to repair service your system when you finally’ve taken it offline. Develop interaction protocols on your internal staff members and also your clients to reassure them about actions you’re using to resolve the condition.
Attackers have just found a method to use this behavior and manipulate it to perform their DDoS assault.
This exploits sure functions in protocols like DNS, NTP, and SSDP, enabling attackers to leverage open up servers over the internet to amplify the quantity of visitors they are able to produce.
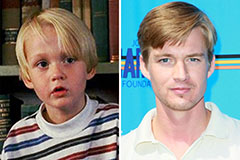 Mason Gamble Then & Now!
Mason Gamble Then & Now! Bug Hall Then & Now!
Bug Hall Then & Now! Meadow Walker Then & Now!
Meadow Walker Then & Now! Pierce Brosnan Then & Now!
Pierce Brosnan Then & Now! Stephen Hawking Then & Now!
Stephen Hawking Then & Now!